Torizon OS Technical Overview
Introduction
Torizon is an Easy-to-Use Industrial Linux Platform that simplifies the development and maintenance of Linux devices. Torizon's primary component is the Torizon OS: an open source minimal Embedded Linux image featuring, among other essential services, an optimal container runtime and components for secure offline and remote over-the-air (OTA) updates, device monitoring and remote access.
- Check the Torizon Supported Hardware
This article provides an architectural technical overview of Torizon OS and explores its main components and the tools to work with the system. For step-by-step instructions to start working with Torizon, please see the Torizon Quickstart Guide.
Torizon OS Images
The table below shows a comparison between the currently supported Torizon OS image variants:
| Image | Intended use |
|---|---|
| Torizon OS Easy Pairing | Evaluation-focused image with included app to help with pairing to the Torizon Cloud and deploying evaluation containers |
| Torizon OS | Pre-built binary image, with container runtime included - meant to support workflows using Torizon tooling and development with containers |
| Torizon OS Reference Minimal Image | Pre-built reference image for Torizon OS without containers - meant to support Yocto workflows |
There are additional images in our Toradex Easy Installer CI feed labeled as experimental.
Developers should be aware of these images' limitations for production scenarios.
Note that in most cases you will not use the prebuilt Torizon OS images directly on target hardware after evaluation, but rather as input to your customization workflows.
Learn more about the evaluation containers in the section Container Runtime: Docker.
Torizon OS Development Options
There are three main sets of workflows for Torizon OS Development:
- Torizon OS with Torizon customization tools: This is the traditional workflow for Torizon users. The Torizon OS image is provided as a pre-built binary, and tools such as TorizonCore Builder are used to customize the operating system for your needs. Application development is normally implemented inside Docker containers, and the Torizon IDE Extension is normally used by application developers.
- Torizon OS Reference Minimal Image with Yocto: This setup uses standard Yocto workflows for both OS and Application development, and does not include the Docker container runtime. This is an efficient way to integrate secure updates and IoT management into Yocto workflows.
- Torizon OS + Yocto: This allows you to deeply customize the OS using all the features that Yocto provides while maintaining the flexibility of additional customization using TorizonCore Builder and Docker. This option is just a combination of the previous two and will not be documented separately.
Torizon Architecture

Linux Kernel
Torizon OS is built on top of Toradex Linux BSPs. An in-house software development team works with the hardware team to design and maintain high-quality Linux BSPs targeting production devices.

Some characteristics of the Torizon OS image:
-
Toradex provides Torizon OS in a pre-built binary image. This image features essential command-line utilities and a reasonable amount of peripherals enabled in the Linux kernel. Hence, for most of the use cases, the usage of these binaries is the most recommended approach to design the application, and it is unnecessary to re-build Torizon OS from the source.
-
In cases in which image re-building and customization are inevitable, Torizon OS is open-source, and Toradex provides instructions to build Torizon OS with Yocto.
-
Toradex maintain its BSPs with updated software for bootloader and Linux kernel following mainline. An exception may exist for recently launched platforms, where the BSP may contain downstream SoC vendor components until Toradex recognizes the mainline efforts are mature enough to be deployed to production.
-
The developers can also follow the Toradex Yocto Project BSP Layers release roadmap and Torizon OS release roadmap page to get updated information about known issues, scheduled bug fixes, and feature improvements.
-
There is no software package management in the base system. The recommended application development and maintenance processes are through the usage of Docker containers.
Torizon updates: OSTree and Aktualizr
Traditional update solutions in the industry, including Torizon Remote Updates and Secure Offline Updates, widely adopt Aktualizr and OSTree technologies. They comprise the part of Torizon updates features that runs on embedded devices.
-
Aktualizr comprises a C++ application working on the client-side of Torizon Remote and Offline Updates. It manages the software update process and implements Uptane, supporting device authentication and provisioning. Aktualizr works alongside OSTree.
-
OSTree is a technology used by Torizon OS to deliver bootable filesystem trees to a device. The basic principle is having a git-like set of work with the filesystem tree.
Root Filesystem
The root file system (rootfs) is the top of the hierarchical file tree. Torizon OS mounts its rootfs as read-only, since it improves device security and reduces the probability of system files corruption. Additionally, it enables rootfs images to be easily updated. Furthermore, to have a read-only root filesystem mounted is a requiremente for OSTree, which is a system adopted by Torizon to perform upgrades of filesystem trees.
However, there are two special cases. OSTree preserves /etc and /var during upgrades, implying that they are writeable directories (rw). On those cases:
-
/etc: It is upgraded by OSTree by a 3-way merge. It means that, during the upgrade process, OSTree will apply any local changes to the new copy, while leaving the old untouched. For more information, refer to OSTree documentation. -
/var: This directory is not managed by OSTree. In this case,/varis not touched by OSTree at all, and shared between all of its deployments.
Torizon OS Customization Tooling
System developers can easily customize the operating system image to meet their needs using the TorizonCore Builder tool, which enables users to easily make common changes to their underlying operating system image without needing to use the more complex Yocto-based workflows.
Typical examples of these changes include:
- Adding a custom splash screen
- Adding an out-of-tree kernel device driver
- Modifing a device-tree overlay
- Adding custom configuration files, such as Wi-Fi credentials
Torizon OS is open-source and built with Yocto. You may want to build Torizon OS with Yocto for some reasons:
- You are a Yocto Project expert and would like to develop your applications working with a familiar toolchain;
- You need to perform customizations beyond Torizon tooling support.
Yocto development support includes default Torizon OS with containers and Torizon OS Yocto Reference Image Minimal without containers.
Torizon OS Application Development
Yocto: Traditional Development
As mentioned above, Torizon development supports traditional Yocto workflows for OS customization and also application development with the Torizon OS Yocto Reference Minimal Image.
Containers: Modern Development
One of the advantages of the Torizon OS is the possibility to work on application architectures based on containers. This modern software development architecture provides significant benefits such as modularity, scalability, integration, and distributed development. There is no processing performance impact using containers, as it runs on the same base OS kernel.
Read more on our dedicated blog.
Docker: Container Runtime

By the definition available on the Docker website:
A container is a standard unit of software that packages up code and all its dependencies, so the application runs quickly and reliably from one computing environment to another. A Docker container image is a lightweight, standalone, executable package of software that includes everything needed to run an application: code, runtime, system tools, system libraries, and settings.
- Docker engine enables the execution and management of containers in the device.
- Toradex provides Docker container images based on Debian designed for the usage with its Computer on Modules
- Docker daemon starts automatically after boot. It is possible to start containers automatically with the daemon.
- Torizon OS images available for online installation with Toradex Easy Installer come with containers pre-provisioned focused on development:
- Weston
- Chromium
- Container with Development Tools
- To simplify the customer's production process, Toradex provides the possibility for developers to download Torizon OS images with no containers pre-provisioned and combine it with his own containers, generating a monolithic element to deploy on the board.
Torizon OS Debian Containers

Application developers will take advantage of the Torizon OS Debian based containers images as a starting point for their Dockerfiles.
Below are some highlights of the Debian Containers:
- The images are open-source;
- Uses the slim release of Debian;
- Contains group permissions necessary to access hardware peripherals and recommended software packages for execution in Toradex modules;
- Graphical container images with Weston/Wayland/XWayland and GPU support are also available for some modules.
See the Toradex Debian based containers images article for in-depth information.
Integrated Development Environment (IDE) support
Toradex provides a Visual Studio Code extension to work with Torizon OS: Torizon IDE Extension.
Other Toradex and 3rd Party Containers
- The Torizon resources article lists the ready-to-run demonstration 3rd party containers that Toradex offers in partnership with different industry segments and technologies.
- The List of Container Images for Torizon has brief information about the containers maintained by Toradex and partners.
- Visit the Dockerhub page to find out other available Docker containers targeting execution in ARM architecture.
Torizon OS Yocto Reference Minimal Image
Torizon OS Yocto Reference Minimal Image is an embedded Linux reference image built on top of Toradex Linux BSP Layers. As with every other reference image from Toradex, Torizon OS Yocto Reference Minimal Image is a starting point for the development process of our customers.
It inherits all the configurations, device drivers, and kernel modules from Torizon OS, including the components for secure offline and remote over-the-air (OTA) updates. For more information, refer to the section Torizon updates: OSTree and Aktualizr. However, the Reference Minimal Image does not feature the Docker engine. This means it is not possible to use Docker containers out of the box in this environment.
Torizon OS is a pre-built binary image that can be customized using Torizon’s default tooling, including Docker, Visual Studio Code extensions, and TorizonCore Builder. It enables developers to easily deploy and manage container-based applications without rebuilding the OS from source.
In contrast, the Torizon Reference Minimal Image serves as a Yocto-based reference image, intended for developers who need deep customization at the operating system level. It provides the foundational components of Torizon without containerization, allowing integration and modification within a Yocto SDK environment. This is shown in the diagram below:
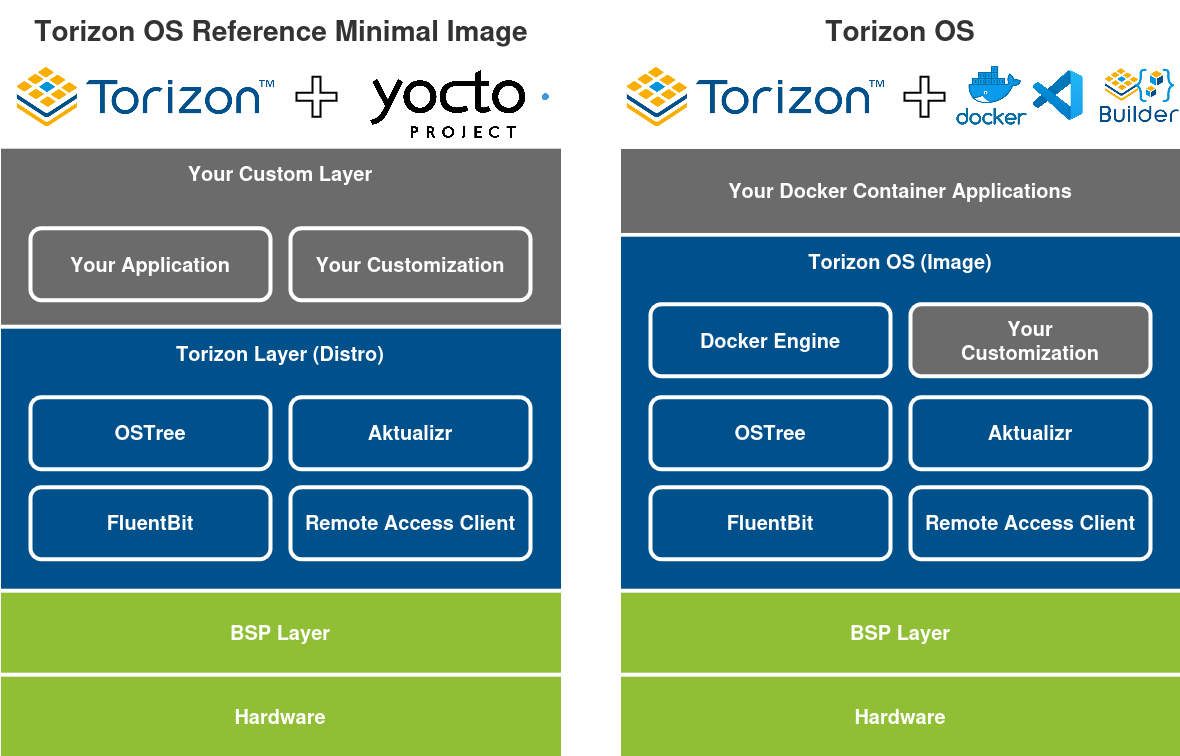
Unlike Torizon OS, the Torizon OS Yocto Reference Minimal Image is not a ready-to-use operating system!
Furthermore, the notable difference from the Torizon OS is that Torizon OS takes the basic elements of the reference image and adds the container runtime resources, making it a ready-to-use Linux-based operating system for you to develop your application. If you are looking for more information about Torizon OS, refer to Torizon OS Technical Overview.
Some characteristics of the Torizon OS Reference Minimal image:
-
Toradex offers a pre-built binary image of Torizon OS Reference Minimal that contains only the essential command-line utilities. This image is designed solely for testing purposes and should not be used in a production environment. It is highly recommended to use Yocto Project to add your application, and customize and re-build the Torizon OS from source by using its reference image as a base. This approach ensures that the final image is tailored to meet your specific needs and does not require the usage of containers.
-
As is Torizon OS, the reference minimal image is open-source. Toradex provides the necessary instructions to build it with Yocto.
-
Toradex maintains its BSPs with updated software for bootloader and Linux kernel, preferably using mainline components. In recently launched platforms, the BSP may contain downstream SoC vendor components until Toradex recognizes the mainline stack as mature enough to be deployed to production.
-
The developers can also follow the Toradex Yocto Project BSP Layers release roadmap and Torizon OS release roadmap page to get updated information about known issues, scheduled bug fixes, and feature improvements.
Regardless of which Development Option you choose for working with Torizon OS, the following characteristics will be applicable.
Intended Use
Torizon OS Yocto Reference Minimal Image aims to enable and facilitate the development on Torizon OS using Yocto Project/OpenEmbedded without containers, while enabling the usage of Torizon Cloud features.
Torizon OS Yocto Reference Minimal Image gives a starting point for the customization, offering the base Yocto layers used to build your operating system with the minimum requirements. To customize the reference image and have an operating system suitable for your specific needs, first, you have to understand the basics of the Yocto Project. Then, it is important to:
- Understand about Toradex reference images offerings: refer to BSP Layers and Reference Images for Yocto Project Software.
- Understand about how to build a Toradex reference image: refer to Build a Reference Image with Yocto Project/OpenEmbedded and Build Torizon OS from Source With Yocto Project/OpenEmbedded.
- Understand the process of creation and customization of layers: refer to Custom meta layers, recipes and images in Yocto Project (hello-world examples).
Torizon on Debian/Ubuntu: Torizon Connector
Torizon Connector is an installation app that simplifies the installation of the Torizon software stack — including Torizon OS components and dependencies — on Debian based host systems.
It enables developers to set up and manage the Torizon environment from familiar apt-based environments.
- Fetches and installs key components of the Torizon ecosystem, streamlining development on Debian/Ubuntu hosts.
- Provides an unified, script-based approach to configure tooling, packages, and base images necessary for developing with Torizon.
- OS updates via OSTree are not supported with this approach.
Refer to:
Additional Resources
Blogs
Visit the Blog section of Torizon.io and the Engineering at the Edge Blogs.
Webinars
Visit the On-Demand Webinar section of Torizon.io.